After my last blog post about Hurl, someone asked me, and I quote: "... why?" The simple answer is "for the joke." But the longer answer is that useless software is a fantastic way to explore and experience the joy of computing. Play is an important part of exploration and joy.
Many sites have been affected by the aggressiveness of web crawlers designed to improve LLMs.
I’ve been relatively spared, but since the phenomenon started, I've been looking for a solution to implement.
Today, I present a zip bomb gzip and brotli that is valid HTML.
I love it when I get email from readers. It's spawned blog posts before, and this time, well, it's going to happen again. This time though, I'm going to publish my reply for the world to see because, well, in truth, I'm a lazy human that enjoys linking to what I've said rather than typing everything out, again. Yes, this is a very cheap way to get you to my website. Moreover though, why would I reply on social media when I've already written it down elsewhere? That just seems silly!
I get all kinds of email. This one made me scratch my head.
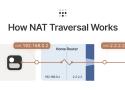
We covered a lot of ground in our post about How Tailscale Works. However, we glossed over how we can get through NATs (Network Address Translators) and connect your devices directly to each other, no matter what’s standing between them. Let’s talk about that now!
Rendering text, how hard could it be? As it turns out, incredibly hard! To my knowledge, literally no system renders text “perfectly”. It’s all best-effort, although some efforts are more important than others.
Back in 2017, I was building a rich text editor in the browser. Unsatisfied with existing libraries that used ContentEditable, I thought to myself "hey, I'll just reimplement text selection myself! How difficult could it possibly be?" I was young. Naive. I estimated it would take two weeks. In reality, attempting to solve this problem would consume several years of my life, and even landed me a full time job for a year implementing text editing for a new operating system.
A few years ago, my cat gave me my most memorable middle of the night software engineering incident. I was working at a startup, and we didn’t have a formal on-call rotation yet. That was a deliberate decision, since being on-call is painful, and the team was good about just collectively keeping an eye out for urgent alerts. We eventually set up an on-call rotation, but before that happened, I had a fun night.
Hello friends! Hope your weekend plans did not go to shit because of some open source library you have no clue if it's being used in your environment or not because, well, let's face it: nobody fucking knows these things. Nobody has time for this. YoloOps is alive and well, boys!
Here's the thing that you will absolutely see written everywhere by some dumbass sycophant: "We need to secure the software supply chain!" Sure thing, bro. One problem, though: in order for a supply chain to be a supply chain, the chain must be comprised of suppliers. The masochist hero maintaining that library you just npm install without even thinking about it is not your fucking supplier.
Ever hear one of those stories where as it unravels, you lean in ever closer and mutter “No way! No way! NO WAY!” This one, as far as infosec stories go, had me leaning and muttering like never before. Here goes:
Last week, someone reached out to me with what they claimed was a Spoutible data breach obtained by exploiting an enumerable API. Just your classic case of putting someone else's username in the URL and getting back data about them, which at first glance I assumed was another scraping situation like we recently saw with Trello. They sent me a file with 207k scraped records and a URL that looked like this...
how one little joke can get so, so out of hand
Every once in a while I took a look at the various services I self-host and think to myself? Is hosting $X service by myself really worth the cost? What is the cost? Would paying someone to host said service be more cost efficient?
That got me thinking about, what are the costs of self hosting? Let’s talk about it.
This post is dedicated to the memory of Niklaus Wirth, a computing pioneer who passed away January 1st. In 1995 he wrote an influential article called “A Plea for Lean Software”, and in what follows, I try to make the same case nearly 30 years later, updated for today’s computing horrors.
The most important lesson to figure out is why it is taking so long to restore services. That will tell us how to prevent such a calamity in other vital national institutions.
I run my own Matrix homeserver that I share with friends and family. Ever since I started working for Element back in February of 2020, I've learned a lot more about the Matrix protocol and what's possible to do with it. During a conversation with a few privacy minded friends that use my HS (HomeServer), I pointed out that the admin of a homeserver has a lot of power over their accounts and that they as users explicitly trust the admin. In this post, I want to explore and document the ways a malicious admin can mess with the privacy of a Matrix account. Note: malicious admin in this case can also mean a hacked admin.
Recently I came across a puzzling fact: the International Criminal Court hashes electronic evidence with MD5, even though MD5 is badly broken. So, why are lawyers using broken, outdated technology? The answer involves the common law system, cultural isolation, and a single man named Don L. Lewis.
Sometimes, making particular security design decisions can have unexpected consequences. For security-critical software, such as password managers, this can easily lead to catastrophic failure: In this blog post, we show how Bitwarden’s Windows Hello implementation allowed us to remotely steal all credentials from the vault without knowing the password or requiring biometric authentication. When we discovered this during a penetration test it was so unexpected for us that we agreed with our client to publish a blog post about it and tell the story.
Searching the Internet for information sucks. We live in an age of information surplus. At any point in the internet there are an unimaginable number of things to read, watch, listen to, and play through. The average person's backlog of entertainment stretches for several lifetimes.
It is impossible to consume all of the information on the Internet. It was impossible even when the Internet was much smaller. Much, much smaller.
John Graham-Cumming wrote an article today complaining about how a computer system he was working with described his last name as having invalid characters. It of course does not, because anything someone tells you is their name is — by definition — an appropriate identifier for them. John was understandably vexed about this situation, and he has every right to be, because names are central to our identities, virtually by definition.
So, you’ve been invited to an unconference! Maybe you’re not entirely sure what that means (did the organizers misspell "conference"?), or maybe you’ve been to dozens of these before and you’re looking for some ideas for how to run an awesome session.