Hi! This is my Shaarli server, a site where I will be adding random links to talks and blog posts I find interesting or inspiring. Maybe if you look around you'll find something interesting too.
My homepage: ivyfanchiang.ca
After my last blog post about Hurl, someone asked me, and I quote: "... why?" The simple answer is "for the joke." But the longer answer is that useless software is a fantastic way to explore and experience the joy of computing. Play is an important part of exploration and joy.
CSS is a programming language, and you can make games in it. Let's install NoScript and make some together!
This talk is about how HTML and CSS can be used to make interactive art and games, without using any JS or server-side code.
I'll explain some of the classic Cohost CSS Crimes, how I made CSS Clicker, and what's next for the CSS scene.
I hope this talk will teach and/or inspire you to make cool stuff of your own!
84 million requests a second means even rare bugs appear often. We'll reveal how we discovered a race condition in the Go arm64 compiler and got it fixed.
Written by my friend Teddy :D
There are certain very critical questions that it is important to ask oneself before a major endeavor, especially if there is risk involved:
"How far and how high will I climb this mountain and when will I turn around if the weather changes or if my health or my equipment doesn't hold out?"
"How much money am I willing to risk at this casino before I call it and walk away, no matter what my odds look like in that exact moment?"
And the big one that we will talk about today: "What work would I be willing to do in order to earn money that could have significant ramifications in my life and the lives of those around me?"
In some ways, this talk will be a reflection and continuation on themes that were covered by another speaker last year at BSidesRDU. I hope that we can expand on this topic and discuss together with one another what the right path looks like for people who are considering their journey through tech, hacking, and the INFOSEC industry.
Many sites have been affected by the aggressiveness of web crawlers designed to improve LLMs.
I’ve been relatively spared, but since the phenomenon started, I've been looking for a solution to implement.
Today, I present a zip bomb gzip and brotli that is valid HTML.
I love it when I get email from readers. It's spawned blog posts before, and this time, well, it's going to happen again. This time though, I'm going to publish my reply for the world to see because, well, in truth, I'm a lazy human that enjoys linking to what I've said rather than typing everything out, again. Yes, this is a very cheap way to get you to my website. Moreover though, why would I reply on social media when I've already written it down elsewhere? That just seems silly!
I get all kinds of email. This one made me scratch my head.
I love Linux. I use Linux. It has its advantages.
It’s responsive—sometimes. Some things just work plain better. Settings being stored in actual config files instead of opaque registries? That’s an accessibility win. When something breaks, you don’t have to reinstall the whole OS like you would on Windows. Most importantly: it’s mine. To do with as I please. To fix, break, rebuild, and own.
And let me be clear: This post is not an attack on the people who maintain Linux accessibility.
A bug in a scraper script led to us downloading every single native library in every single Android app ever published in any market (~8 million apps).
Instead of deleting this massive dataset and starting again, we foolishly decided to run some binary similarity algos to check if libraries and outdated and still vulnerable to old CVEs. No one told us we were opening Pandora's box.
A tragic story of scraping, IP-banning circumvention, love/hate relationships with machine learning, binary similarity party tricks, and an infinite sea of vulnerabilities.
Remember the days when faxes were the pinnacle of office tech, and the sound of a paper getting pulled in was as satisfying as a fresh cup of coffee? Well, it's time to dust off those memories and reintroduce ourselves to the quirky world of printers and their forgotten fax interfaces – yes, those relics that make us all feel like we're in an '80ies sci-fi movie – and specifically, how they can unlock a new frontier in printer security exploits!
You've probably already heard the story: we got contracted to analyze a bunch of trains breaking down after being serviced by independent workshops. We reverse engineered them and found code which simulated failures when they detected servicing attempts. We presented our findings at 37C3… and then shit hit the fan.
How is 3DS preservation faring 10 years after the release of the first emulator? What technical obstacles have we overcome, which ones remain? What hidden gems have we discovered beyond games? Join us on a journey through the struggles, the successes, and the future of 3DS emulation!
Ever wondered what happens behind the scenes when you click buy on that domain for a new side project that'll definitely happen (you will get to it eventually, right)? Well this is the talk for you! We'll cover all the extremely cursed details of how exactly one sells and manages a domain, the standards for this (or lack thereof), and some pointers for how you could get started managing your own domains directly, if you're not completely put off by this talk's contents.
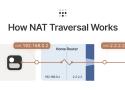
We covered a lot of ground in our post about How Tailscale Works. However, we glossed over how we can get through NATs (Network Address Translators) and connect your devices directly to each other, no matter what’s standing between them. Let’s talk about that now!
The enshittification of the internet wasn't inevitable. The old, good internet gave way to the enshitternet because we let our bosses enshittify it. We took away the constraints of competition, regulation, interop and tech worker power, and so when our bosses yanked on the big enshittification lever in the c-suite, it started to budge further and further, toward total enshittification. A new, good internet is possible - and necessary - and it needs you.
SQL injections seem to be a solved problem; databases even have built-in support for prepared statements, leaving no room for injections. In this session, we will go a level deeper: instead of attacking the query syntax, we will explore smuggling attacks against database wire protocols, through which remote, unauthenticated attackers can inject entire (No)SQL statements into an application's database connection.
In addition to being certified as a Forensic Locksmith and a Safe and Vault Technician, it sometimes surprises people to learn that I am a Life Safety NFPA & ADA Consultant and Fire Door Inspector. "Deviant, do you make a lot of money doing safety inspections like that?" I get asked. The answer is a resounding no. I didn't take this training for the money, however. I learned about fire doors and fire suppression systems so that I can speak knowledgeably about them if I'm using this field as a cover identity during a break-in job.
This presentation is a comprehensive crash course in the field of National Fire Prevention Association knowledge and building codes. The rundown offered will afford you a lot of useful tips, terminology, and insider knowledge that you can rattle off at an unsuspecting employee or guard who is curious as to what you're doing inside of their building.
What do you do when you’ve found an arbitrary file delete as NT AUTHORITY\SYSTEM? Probably just sigh and call it a DoS. Well, no more. In this article, we’ll show you some great techniques for getting much more out of your arbitrary file deletes, arbitrary folder deletes, and other seemingly low-impact filesystem-based exploit primitives.
Rendering text, how hard could it be? As it turns out, incredibly hard! To my knowledge, literally no system renders text “perfectly”. It’s all best-effort, although some efforts are more important than others.